Beyond the Bench, 10 Unexpected Uses for eDiscovery Tools
When most people think of the term Electronic Discovery (eDiscovery), they think of hordes of document review attorneys scrolling through mountains of electronically stored information (ESI) in preparation for presenting relevant data to the court. While this is one way in which the legal professional uses unstructured data analytics (what we call eDiscovery tools), it is far from the only one.
As the lawyers and case teams begin to think outside the litigation box, they have uncovered many ways to leverage these powerful eDiscovery tools to uncover the truth in electronic documents. By leveraging the eDiscovery process in workflows that do not end up in a district court, they can mitigate risk and extract value from data.
Electronic evidence is relevant not only in civil litigation but also in other areas. New technologies embedded in eDiscovery software is helping a wide variety of industries find relevant data fast. Read on to uncover how the powerful artificial intelligence and machine learning that powers eDiscovery workflows are parsing data sets from HR to Cyber and beyond.
Supercharging Internal Compliance Investigations:
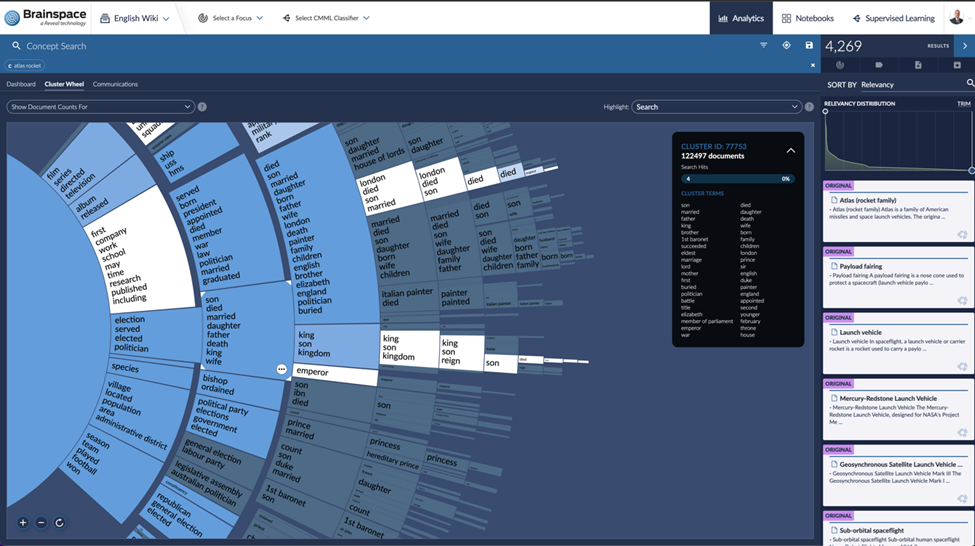
Organizations are often on a mission to sync perfectly with regulations and internal guidelines, and this is no easy feat. Enter the dynamic duo of concept clustering and keyword search. Our tech-savvy heroes for navigating through data jungles.
The former identifies key concepts, issues, and junk fast. Helping the team figure out the who, what, when, where, and why of an investigation lightning fast. The latter helps dive deeper into these keywords and phrases to investigate deeper. Both eDiscovery tools are invaluable for sifting through vast amounts of data and metadata to identify potential compliance issues or breaches. Enabling proactive management and rectification of compliance risks.

Navigating the Murky Waters of HR Investigations:
In the face of allegations like harassment or discrimination, sentiment analysis and email threading come to the rescue. Sentiment Analysis helps you go deeper than the words and phrases on a page, to the emotions and motivations. Email threading weaves together communications across time and people.
These tools dissect communications for emotional undertones, intent, and interpersonal dynamics, providing HR teams with an X-ray vision of the heart of the matter. Whether in email, text messages, social media posts, or other ephemeral forms, these tools can connect the dots. This aids HR departments in understanding the context and seriousness of internal complaints or incidents. Leading to informed decision-making.
Unraveling Fraud Investigations:
Fraud detection within an organization demands a Sherlock Holmes-esque analysis of financial transactions and communications. Here's where Anomaly Detection shines. Often, investigators have days or weeks to sift through terabytes of data, and this can be beyond time-consuming.
By cutting through the noise to highlight patterns and deviations that scream "fraudulent," anomaly detection streamlines the detective work. Making the investigation process both smooth and effective.
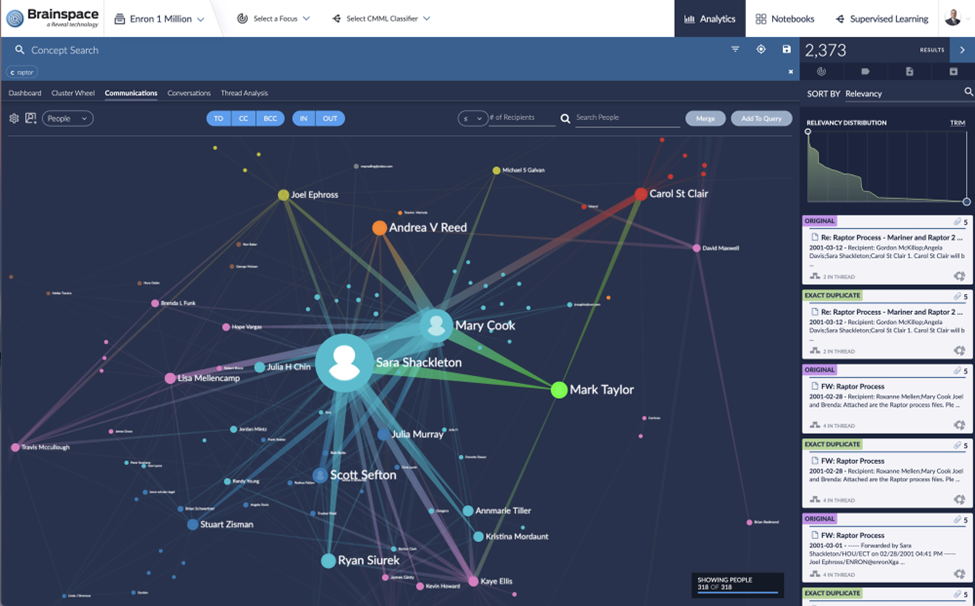
Securing the Fort in Data Breach and Cybersecurity Incidents:
Following a data breach or insider threat, the clock is ticking to understand and remediate. Timeline analysis and social network analysis are the guiding lights, tracing the breach's roots and its spread and pinpointing the exposed data or compromised systems.
These tools are the first responders, driving rapid response and bolstering defenses. No, this is not about social media. Rather about understanding who was communicating with whom using Social Network Analysis. Combining that with timeline analysis is a secret sauce in cyber incident response.
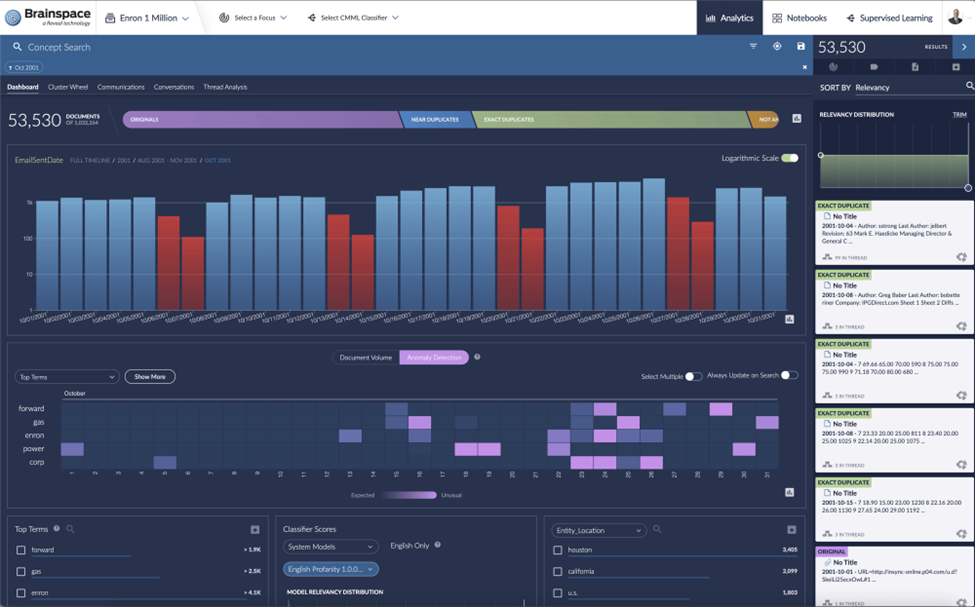
Battling the Specter of Intellectual Property (IP) Theft Investigations:
The specter of IP theft demands rapid and vigilant investigation to protect a company's crown jewels. With Social Network Analysis and data visualization, sifting through documents, metadata and communications becomes a targeted search for clues of unauthorized use or sharing. From laptop, to cellphone, to the cloud all avenues can be woven together to form a single narrative.
Uncovering the who fast and leveraging powerful visual data representation like the communication map and dashboard help investigators find insights fast. It's about fortifying your intellectual assets against threats and keeping your innovations safe and sound. When IP theft is suspected, companies must investigate to protect their assets.
Mergers and Acquisitions (M&A) Due Diligence:
Before Saying ‘I do’ in any M&A deal, due diligence is your north star. This step is critical in guiding you through assessing risks, obligations, and liabilities waiting in the wings.
Concept clustering and AI models expedite the review of critical documents. AI models can be used to carve out noise and surface higher-risk behavior patterns rapidly. Shining a light on the target company's true value and hidden risks hidden in relevant documents. It's about making informed decisions powered by thorough evaluation.
Facing Regulatory Inquiries and Audits Head-on:
When regulatory scrutiny knocks, Covering Your Asset (CYA) with the right documents and records is key. Technology-Assisted Review (TAR) and keyword search are your best allies in this endeavor. Organizing and pinpointing the exact relevant documents needed to demonstrate compliance.
Effective search terms coupled with AI-powered prioritization with TAR help responding parties mitigate discovery costs while still uncovering the relevant electronic information quickly. This approach not only streamlines responses but also minimizes the risk of penalties, keeping you in the clear.
Proactive Risk Management Assessments:
Identifying potential risks before they rise to litigation or regulatory scrutiny is an ongoing quest for organizational safety. Through applying social network analysis, anomaly detection, and timeline analysis to slices of time, we gain insights into the web of internal and external relationships and events.
This proactive stance on risk management is about foreseeing and mitigating threats before they materialize, securing a smoother sail ahead. Regular assessments are vital for identifying potential risks to the organization.
Keep it Confidential With Data Privacy Management:
In a world of GDRP and DSARs and Breaches, oh my, safeguarding personally identifiable information (PII) is paramount. Advanced keyword search capabilities and leveraging PII-trained custom and off-the-shelf Artificial Intelligence models become the guardians of data privacy.
Metadata and the face of electronic documents can be scoured for relevant data and PII using tailor-made AI models with a laser focus on finding the PII before sanctions find you! Ensuring sensitive information is managed and protected in strict adherence to privacy laws.
eDiscovery Outside the Box
Whether you are an in-house lawyer or working on the law firm side, the supercharging power of eDiscovery tools outside litigation cannot be ignored. As the volume of ESI in data sets increases, leveraging these tools can help ensure every relevant document in the gigabytes and petabytes of data is uncovered fast.

