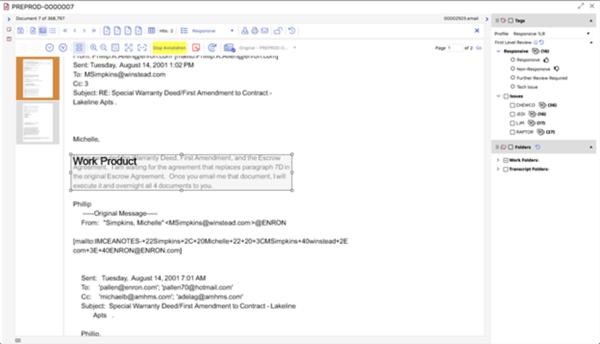
Taming the DSAR Request Beast with eDiscovery Technology
The General Data Protection Regulation (GDPR) gave citizens of the EU a whole host of new and reimagined ways to manage and audit access and use of personally identifiable information (PII). One of the most impactful new rights outlined in GDPR was the right for individuals to access and review the information any organization possesses about them as an individual. This right to access, allows individuals that are EU citizens to access and receive a copy of all information any organization possesses about them via submitting a Data Subject Access Request (DSAR Request).
GDPR and US-based privacy regulation inspired by it, like the California Consumer Privacy Act (CCPA), enumerated new rights and obligations for individuals and the organizations in possession of their data.
The rights under GDPR fall into 8 main categories:
-
The Right to Information.
-
The Right of Access.
-
The Right to Rectification.
-
The Right to Erasure.
-
The Right to Restriction of Processing.
-
The Right to Data Portability.
-
The Right to Object.
-
The Right to Avoid Automated Decision-Making
What the Heck is a DSAR Request?
The right to access is a central component for several other rights provided for under GDPR, namely the Right of Rectification, and the right of Erasure. The right of access is executed by an individual that a company is storing data on submitting a DSAR request in writing, verbally, or even on social media. While data subject right to requests themselves are not necessarily a new thing, the ease with which a requester can submit them has dramatically increased their use.
“The data subject shall have the right to obtain from the controller confirmation as to whether or not personal data concerning him or her are being processed, and, where that is the case, access to the personal data”. -GDPR Article 15
The penalty for non-compliance with DSAR requests is a steep one with fines of up to 4% of a corporation’s annual global turnover or €20,000,000 (whichever is higher). One thing for many organizations to bear in mind is that while litigation and government investigation eDiscovery may not occur at every company, privacy requests can and do. Add to this the fact that recipients of DSARs are only able to refuse to comply with the request in the event the request is “excessive” or “manifestly unfounded'' and the true challenge facing DSAR request recipients comes into focus.
Flavors of DSAR
DSARs come in four main categories, depending on what the requesting data subject wants the responding party to do following the response:
-
General identification of the information collected on customers broadly
-
Information collected on the individual data subject
-
Request to identify and delete all information on a data subject
-
Request to identify, collect and move data subject’s data elsewhere
In the case of GDPR, data subjects may request more than just a copy of all the data held on them. They can request a variety of different types of data including:
-
Confirmation that your organization processes their personal data.
-
Access to all personal information your organization possesses.
-
Your organization’s lawful basis for processing their data.
-
How long your organization stores their data
-
Or the factors used to determine that period, e.g. “as long as you’re a customer”.
-
-
Any relevant information about how the data was obtained.
-
Any relevant information about automated decision-making and profiling.
-
The names of any third parties you share their information with.
Individuals may submit a DSAR to any organization in possession of their personal information to exercise their right to access for any reason. Individuals making a DSAR can do so in a variety of ways including verbally, in writing, or even in a rogue tweet or social media post. The organization receiving the DSAR may only ask for clarifying information to validate the identity of the requestor as the data subject and to facilitate locating and providing the requested information.
How the DSAR Shield Become a Sword
Needless to say, this wild west approach to issuing DSARs has led to a major surge in the volume, variety, and velocity of DSAR issuances and some organizations are struggling to keep their head above water in this DSAR tsunami. GDPR removed the cost barrier and complexity that previously discouraged people from making a DSAR. One additional complicating factor that may not have initially been anticipated is the weaponization of DSAR requests by activists and cybercriminals alike. The result is a steady climb in the volume of DSARS, with a 66% increase just since 2020.
For example, Blizzard faced a wide-ranging 2019 DSAR surge following the video game company’s banning of an individual over vocal support of the Hong Kong protests. Discrete events like a data breach can also spurn on a wave of concurrent DSAR requests that can all but cripple unprepared compliance or legal departments. Additionally, cybercriminals have also used the guise of DSAR requests to obtain personal information for nefarious purposes.
So, what is motivating activists, cybercriminals, and large masses of individuals to wield DSARs as a sword instead of the shield it was anticipated to be? Simply put, a coordinated effort by a large number of people can cost an organization greatly in terms of time, administrative costs, and disruption to normal business practice.
DSARs: Weapons of Mass Disruption
Why are mass DSAR requests so effective at causing organizational disruption? Coordinated mass DSAR requests can create a massive administrative bottleneck for targeted corporations due to the complexity and lack of transparency in many organization’s data infrastructure for client data combined with the pressure of a no more than one month period of time to respond within. There is some precedent for “complex” DSARs receiving extensions of not more than 2 additional months.
Recent studies have found that organizations can have as many as 26 individuals involved in managing the DSAR process and a cost as steep as $1,400 per response absent the right technology to accelerate the review, redaction and identification process. Some larger, multinational, or more notorious information collecting organizations are facing DSAR volumes in the hundred per month.
How eDiscovery Tech Tames the DSAR
For organizations facing the spectre of getting DSAR disrupted, there are a whole suite of eDiscovery tools that can make the process of responding far more manageable. Regulators have the same level of expectations with competent, comprehensive, and timely responses to a DSAR as they would for a litigation or regulatory investigation.
From an execution standpoint, the workflow between traditional eDiscovery matters and DSARs follows much the same overarching path. Potentially responsive material to the DSAR must be identified, processed, reviewed and turned over to the data subject while protecting any potentially personally Identifiable Information in the process.
According to IDC, “data subject access requests…follow identical workflows to that of litigation response. The right eDiscovery provider will be able to quickly and effectively respond to data subject access requests and protect the organization from related compliance violation.”
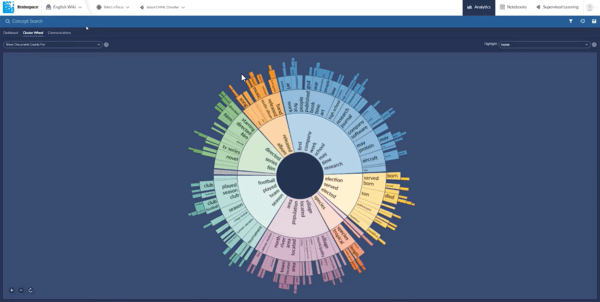
ECA and IG Tools
Information governance exercises of data mapping combined with eDiscovery processes like Early Case Assessment and culling (functionalities like deduplication, filtration and keyword search) can all be employed to dramatically reduce the universe of data involved in a DSAR.
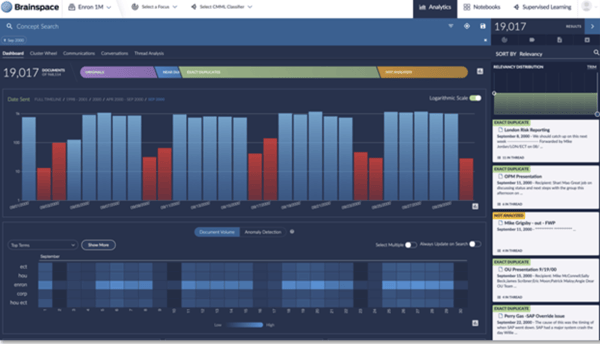
A robust AI-powered review platform and comprehensive data processing capability are key components to an effective DSAR request workflow, especially when dealing with large and disparate data sources.
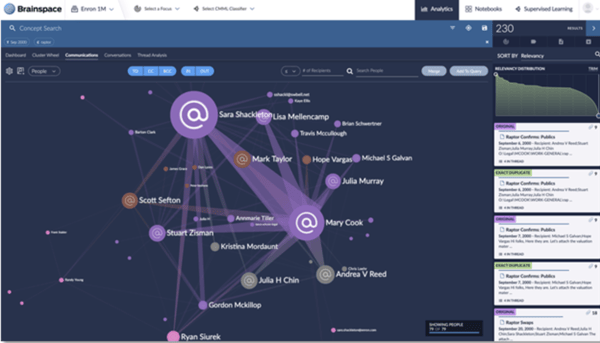
Powerful Culling
Filtering, deduplication, and the application of basic analytics like email threading to more complex PII models can all assist in culling the universe of data that must be reviewed to respond to one or many DSAR requests.
AI-powered concept, custodian and PII identification call all assist in reducing the universe of DSAR response data significantly faster and at a much lower cost for clients.
AI-Powered PII Identification and Redaction
AI-powered PII identification and advanced redaction capabilities like in Reveal enables comprehensive and timely redaction of other individual personal information from the DSAR data set for the response.
This powerful PII identification combined with robust Redaction capabilities dramatically accelerates the ability to respond to a DSAR without placing any other individual’s PII at risk of exposure.
Best Practices for Managing DSAR Requests
While there is no hard and fast methodology for responding to DSAR requests codified in regulation or law, there are best practices widely employed. Below is a step by step guide on how to approach DSARs:
Before Starting the Response
While on it’s face DSAR seems simple enough, the complexity arises in uncovering all of the ways in which an individual's personal data is tracked, maintained or archived across multiple separate and interdependent systems. It is important to have clear understanding of where your data resides, what systems are involved and defensible deletion policies in place to ensure effective and timely DSAR response.
Know thy data
Conduct a comprehensive data inventory before you even begin to approach DSARs. Readily understanding how personal information is stored, shared, and archived is the first step in streamlining your DSAR retrieval and response process. Ensure that you have accounted for structured and unstructured data in a variety of formats.
Additionally, ensure that you are considering newer and emerging data sources that may not have been included in previous data mapping or Information Governance exercises. The language of business has undergone a massive shift in the last 18 months and communication patterns have likewise shifted. Email and structured data may be king, but do not forget that PII might reside in SMS, collaboration tools, zoom chats, ephemeral messaging, or more when scoping and defining the dataverse for your response.
Upon Receiving a DSAR
Wrangle the request
Ensure that you have a methodology for categorizing, organizing, and tracking incoming DSARs and the responses. This process should have a dedicated person or team responsible for receiving, securing, assessing, and responding to DSAR requests. Many organizations have the chief data officer serve as this dedicated resource, with oversight of the DSAR request intake process, data collection, and ultimate response. The organizational methodology can either be in a DSAR specific tracking platform or well-kept spreadsheet depending on the volume and complexity of your DSAR requests.
Validate the DSAR
Because both activists and cyber threats alike understand the value of the PII contained in DSARs it is important to have a standard process to validate the requestor's identity, the necessity of the request, where this is a follow on request, and whether the organization is in possession of the requested information in the first place.
Identity of Data Subject
GDPR specifically requires some form of digital validation of the requesting subject. In validating identity, do not request PII like Social Security numbers of ID due to risk of breach among other validation issues. Most organizations simply use the same means initially used by the company to verify a subject’s identity within their org. (i.e. email request sent from the same email). For more sensitive data, questions based on knowledge only the data subject would possess can be employed or a combination of login/password. Absent adequate validation an organization is completely within their rights to reduce to process the DSAR and inform the data subject as such.
Validate the Request Itself
Recipients of DSARs should also clarify the request if it is not immediately clear what the requestor is demanding as well as determine what their obligation to respond is. In the event the request is “manifestly unfounded” or excessive it is within an organization's rights to deny it.
What qualifies as excessive and manifestly unfounded per the ICO?
-
the individual has explicitly stated, in the request itself or in other communications, that they intend to cause disruption;
-
the request makes unsubstantiated accusations against you or specific employees;
-
the individual is targeting a particular employee against whom they have some personal grudge; or
-
the individual systematically or frequently sends different requests to you as part of a campaign with the intention of causing disruption, eg once a week.
-
repeats the substance of previous requests and a reasonable interval has not elapsed;
-
overlaps with other requests.
Identify, Collect & Process the Potentially Relevant Data
If your data mapping and inventory is up to date, the process of data identification and collection for an individual is fairly straightforward. An organization’s IT team should be able to easily export a copy from most internal physical devices, SaaS-based applications like O365, and various other collaboration tools. eDiscovery tools like data processing, deduplication and deNISTing, email threading, and AI-powered PII identification can all be used to reduce the volume of data outside of the scope of the request that requires review.
Review and Redact for PII
In complying with a DSAR, it is imperative that the responding organization does not inadvertently violate another individual’s data privacy rights in the process. After using AI-powered analytics like Reveal to eliminate non-responsive data, duplicate information, and false positives, the data should be thoroughly reviewed.
This step is both to ensure that the correct requested information is all present and that no other individual’s PII is present. PII models in combination with human reviewers should be utilized to ensure all potential PII for individuals other than the data subject are redacted to preserve the non-data subject’s right to privacy.
Respond to Requester
Within 30 days, the data subject issuing the DSAR request must be responded to in a clear and jargon-free manner. Once the relevant data is identified, the responding party should inspect the data, determine the format and add any extra information deemed relevant.
The data and full response should be packaged and provided within 30 days to the data subject. The response should be as comprehensible as possible, especially if the request is for “everything” withholding any material could be construed as violating the right to access under GDPR. The data can either be provided as the raw data if it is an easy to access data type or “remote access to a secure system which would provide the data subject with direct access to her or her personal data” per recital 63 of GDPR. The request ought to also include a reindeer of the subject’s data privacy rights at the conclusion of the response.
Demonstrate Compliance
To comply with GDPR, an organization must be able to demonstrate its compliance with the DSAR requests in a timely manner. To facilitate this demonstration, organization must maintain accurate and up to date records of the following:
-
All Received DSARs
-
Data subject contact information for each DSAR
-
Description of the request
-
When and how the Request was made
-
Who made the request
-
Whether the DSAR was rejected or replied to
-
Date of response or time taken to respond
What Does the DSAR Future Hold?
The velocity of DSAR requests, both weaponized and general, is only going to increase in the coming years. The steady growth of GDPR driven DSARs in combination with recent US-based data privacy laws including most notably CCPA, the velocity of DSARs facing organizations of every size is continuing to grow.
Taking a brute force approach to responding to DSARs can involve as many as 26 individuals and a cost of as much as $1,406 per request without an effective technology solution in place. Savvy organizations looking to create a seamless, efficient process and workflow to manage the surge in DSARs are well served to look at the leading technologies surfacing key facts and reducing time to evidence in eDiscovery.



.png?width=1000&name=dsar%20request%20(1).png)