The 'Who' in the Whodunit: Unraveling PII in eDiscovery
Today we are at the crossroads of privacy and technology. A place where data and identity collide. When it comes to eDiscovery, there is an 800 lb. risky guerilla swimming in the sea of data, waiting to pounce. It's the massive risk posed by the mishandling of Personally Identifiable Information (PII) in eDiscovery.
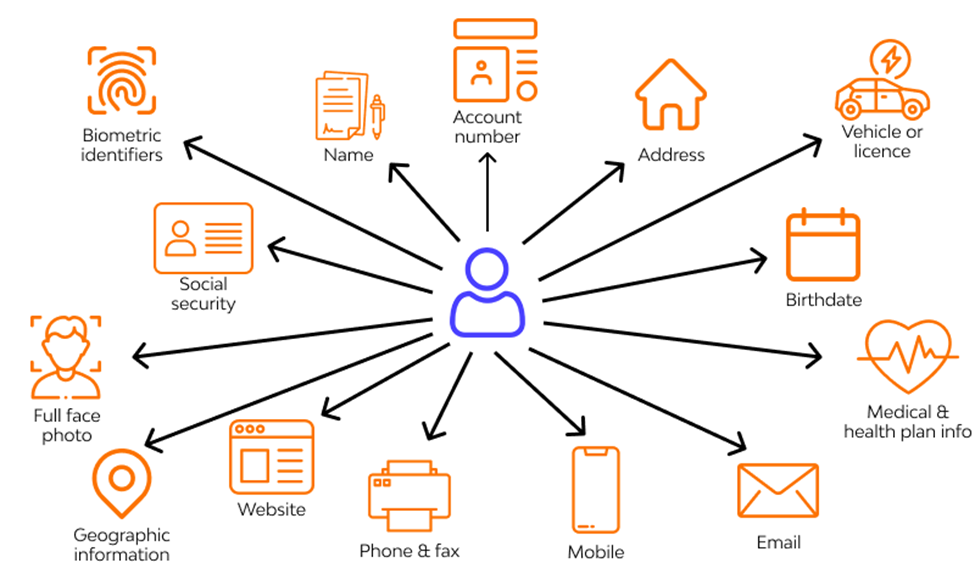
Now, PII is more than just your name, address, or phone number, folks. It's any data that can potentially identify a specific individual. We're talking the big stuff - social security numbers, bank account details, even email addresses. As well as things that you might not expect to be PII ... like your internet browsing history (eeeek!)
Here's a fun fact for you: the concept of PII emerged with the rise of digital databases in the late 20th century. Imagine that - PII is younger than the Internet! But that does not mean this juvenile personal data protection concept is something to ignore.
We must handle PII with care... or face dire consequences.

The ABCs of PII
First off, what's PII anyway?
In the most basic terms, it's any data that could potentially identify a specific human being. Your name, your email, your social security number - all these are pieces of PII. It's the foundation of personal privacy in our interconnected world.
Below is a quick rundown of all the types of Personally Identifiable Information, or PII, you might run into during eDiscovery:
- Names: All kinds, folks! Full names, maiden names, even aliases. Any name that's been used to identify a person.
- Personal Identification Numbers: The big ones like Social Security numbers (SSN), driver's license numbers, and even those sneaky passport numbers.
- Addresses: Digital and physical. We're talking email addresses, home addresses, you name it!
- Phone Numbers: Whether it's a home, work, or cell, it counts!
- Personal Traits: This can get a bit CSI - photographs, fingerprints, even handwriting.
- Biometric Data: Now we're in sci-fi territory. Think retina scans and facial geometry.
- Demographic Information: Everything from date of birth to marital status, and even religion.
- Work Info: We're looking at job titles, salary information, work addresses, and anything else about where and how someone works.
- Health Info: This is a sensitive one, folks - we're talking medical conditions, health records, and insurance information. Although these are also subject to Personal health information (PHI) regulations like HIPAA.
- Educational Info: From the schools attended to the degrees earned, it all counts!
- Financial Info: Those crucial bank account numbers, credit histories, credit card numbers and even purchase records.
- Internet Activity: Welcome to the digital age, where even your IP address and social media profiles are PII!
This list is like the Internet - vast and ever-expanding! Remember, context matters, and what might be PII in one situation may not be in another. When handling such data, let's channel our inner superheroes.
Protect personal data with all we've got by following all data protection laws and regulations during the eDiscovery process. Putting on your data protection cap for a wide variety of types of data which may contain the types of information that constitute PII.
How is PII Related to eDiscovery?
As we have previously discussed, eDiscovery is the detective work of the digital world. It's a process where we're searching, locating, securing, and sometimes even taking an ai-powered magnifying glass to electronic data. All with one goal in mind: using it as evidence in a legal case.
When PII collides with eDiscovery, things get interesting. The stakes? High as ever, with both legal implications and people's privacy on the line.
When we're doing our digital detective work, we've got to handle that PII with care. This isn't about just solving a case, it's about protecting PII in the process. Think about it: if a company's tangled up in a lawsuit and they're going through eDiscovery, they can't just spill the beans about their customer’s or employees’ sensitive information to everyone and their mother.
Because Discovery often deals with sensitive PII, it can be a target for data breach or unauthorized access. It is important to protect the personal identifiers of data subjects, custodians, and more in the discovery process. Redaction, precise retention, and security controls can all help to safeguard PII from cybersecurity and data privacy risks.
The Golden Rules: Protecting PII during eDiscovery.
So how do we keep our balance amidst this digital juggling act? Follow these golden rules on how to protect PII during the eDiscovery thrill ride.
- Scope it Out: Uncover the full landscape of your PII - conduct comprehensive data mapping and know what you're working with. No detective starts a case without first understanding the players involved.
- Sort with Sophistication: Tier your data based on sensitivity, using a data classification framework. It's like sorting clues based on their importance to your case.
- Controlled Access: You wouldn't let just anyone wander through your crime scene, would you? Well, the same goes for a minefield of PII in a document review data set. Implement Role-Based Access Control (RBAC) or Attribute-Based Access Control (ABAC) to safeguard PII.
- Cipher Mysteries: Keep your PII under lock and key with encryption. It's like using a secret code only your team knows.
- Redaction Action: When discovery calls for sharing, keep private data private by using advanced redaction tools. It's like blurring out sensitive parts of a surveillance photo.
- Audit Trails: Create a breadcrumb trail showing who accessed your data and when, using robust auditing and logging systems. Every good detective keeps meticulous records, right?
- Security by Design: Don't slap on your security measures like a Band-Aid - embed them right into your eDiscovery process. That's your Security by Design and by Default.
- Stay Up to Date: Keep your protective gear on the cutting edge - use timely patches and version updates to your data protection software. Even our tech tools need tune-ups!
- Continuous Learning: Sharpen your team's skills with regular training on the latest PII protection best practices. A good detective never stops learning!
- Incident Response Plan: Have a contingency plan - your very own Incident Response Plan - for those "uh-oh" moments when a data breach happens. Because every good detective story has its twists!
There you have it, my fellow data detectives. Let's keep up the good work, respecting the PII in our care as we unravel the mysteries of our digital world. This is TechnoCat, Cat Casey, signing off until our next adventure. Stay savvy and stay safe!
Why Should We Care About PII in eDiscovery?
These aren't just nice-to-have practices; they're mandated by major data privacy laws around the globe. The King Kong of privacy regulations is undoubtedly the General Data Protection Regulation (GDPR) in the EU.
But the California Consumer Privacy Act (CCPA) in the Golden State falls close behind. And many other regional data privacy laws designed to protect data and require us to handle PII with the utmost care. Or else...
They're not just suggestions, they're rules to live by. They demand that we protect PII, not just in our daily lives but especially during eDiscovery.
Now PII is related to personal identifiers, but information that is related to health falls under a different category. Personal Health Information (PHI) is regulated by HIPAA as well as privacy regulations like GDPR and CCPA. It still must be protected but has different regulatory requirements and penalties.
As we put on our digital detective hats, the delicate equilibrium between tech advancement and privacy protection becomes more crucial. Remember, while we're sleuths in the digital frontier, we're also the guardians of personal data. So, let's tread lightly.
What Happens When Things Go Wrong With PII?
So, what happens when things go sideways with PII in eDiscovery? Firstly, let's make no bones about it – mistakes with PII during eDiscovery can lead to some severe consequences. We're not just talking a slap on the wrist here. It's serious business, folks.
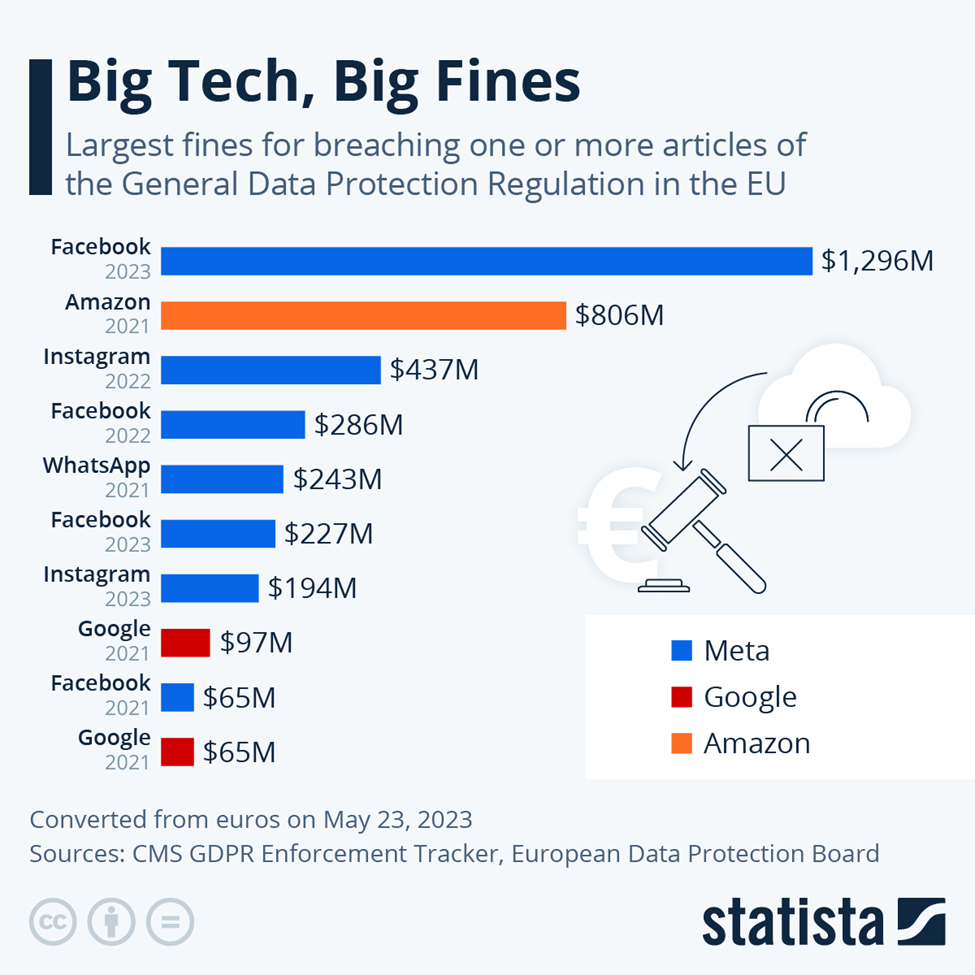
- Legal Penalties: Depending on the jurisdiction, messing up with PII can lead to substantial fines and penalties. Over in the EU, GDPR violations can result in fines of up to 4% of a company's global annual turnover or €20 million, whichever is higher. Ouch! On home turf, the CCPA in California can slap fines of up to $7,500 per violation. And trust me, those fines can add up pretty fast.
- Civil Lawsuits: Companies that go rogue with PII can also face civil lawsuits from individuals whose PII has been mishandled. These lawsuits can result in heavy damages awarded to the plaintiffs, and let's not forget the cost of litigation itself.
- Reputational Damage: Now, this is a biggie. In today's world, trust is a currency, and if a company loses that, it's a steep uphill climb to regain it. Mishandling PII can lead to a massive loss of trust among customers and partners, affecting business relationships and bottom lines. Think of the egg on Capita One’s face when the hacker was bragging about stealing 140,000 client records with SSN and more PII on social media or
- Operational Impact: Don't forget, folks, when legal and compliance teams are tied up with investigations and remediation following a PII snafu, they're not doing their regular work. That's a hidden cost that many don't consider until they're knee-deep in it.
- Regulatory Scrutiny: Once a violation occurs, expect regulatory bodies to have you under their microscope. This increased scrutiny can lead to more rigorous audits and an ongoing need to demonstrate compliance.
From Service providers to Law firm or in-house counsel we all have an obligation to protect PII throughout our discovery and document review workflow. Data Security is especially critical when PII is present. And the stakes outlined above highlight why the extra effort is merited with PII.
A TechnoCat Challenge
Now, here's a little challenge for you, my fellow eDiscovery enthusiasts. Take a step back and evaluate your current eDiscovery practices. Are you handling personal data with the care it deserves? Is there room for improvement when it comes to sensitive data?
I'd love to hear your experiences and thoughts in the comments.
So, digital detectives, the moral of the story? Be careful, be diligent, and handle that PII with the respect it deserves. Remember, with great data comes great responsibility.

