Outside The Litigation Box: Epic eDiscovery Secrets For Non-litigators
There is a vast web of software and hardware that powers business and personal life today. Last month I wrote about the vast digital web that litigators must navigate to uncover key facts and evidence. But this ever-expanding dataverse is not just for litigators.
The Federal Rules of Civil Procedure (FRCP) added Electronically Stored Information (ESI) to discovery in 2006. As a result, electronic discovery (eDiscovery) was born, but the concept was mainly limited to litigation.
Since then, business challenges involving data have exploded across the legal industry. eDiscovery has expanded to include many uses beyond litigation.
This blog covers what eDiscovery is, how lawyers outside of litigation can leverage it and what to watch out for along the way.
What the Heck is eDiscovery?
Electronic discovery refers to discovery in legal proceedings. This includes litigation, government investigations, or Freedom of Information Act requests. Where the information sought is electronically stored information (ESI).
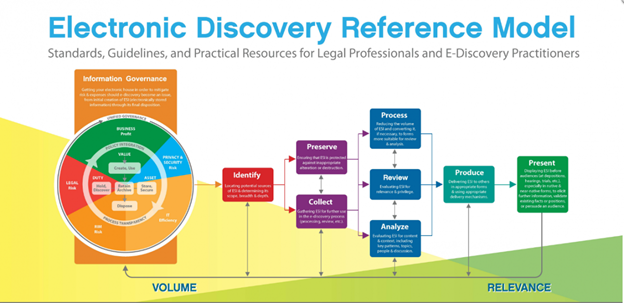
The eDiscovery process follows the Electronic Discovery Reference Model, EDRM for short. The EDRM is a seven-step process following the below phases:
- Identification – Find whose data you want to look at and where it lives.
- Preservation – Prevent people from altering or destroying this data by.
- Collection – Have experts use technology to copy and extract and document the data and metadata (data about the data)
- Processing – Turn 1s and 0s into a reviewable format and get rid of garbage data.
- Review – Use of humans and tech to look at and categorize data by relevance and issues, get rid of more garbage.
- Analysis- Using AI powered tools to quickly gain insights into who is communicating, about what topics to whom in a data set.
- Production – Share the non-garbage data relevant to the matter with interested parties.
In practice, the eDiscovery process may be much messier. There may be many things that cause you to backtrack, repeat a step, or even start the whale darn process over. This is completely normal. Be sure to document your process throughout and work with technology designed to adapt along with you.
-png.png)
Non-litigation Use Cases for eDiscovery
The eDiscovery process outside of litigation, may not have the same starting trigger, but the process remains much the same. The eDiscovery process need not start with the threat of litigation. eDiscovery process maybe started by a regulator, whistleblower activity, or compliance obligation.
Some ways eDiscovery is used outside litigation include:
- Mergers & Acquisitions: In due diligence prior to a merger. Or, to quickly identify the key sources of data a regulator may request as part of a Hart-Scott-Rodino Second Request.
- Data Privacy: eDiscovery software can help identify electronic information about the subject of a Data Subject Access Request (DSAR). The right to request all information in a DSAR General Data Protection Regulation (GDPR) Article 15.
- Cyber: Following a breach, organizations have a regulatory obligation to identify all personally identifiable information. As well as notify affected individuals with a very short amount of time. eDiscovery software and legal AI helps quickly identify and notify affected parties.
- Employment: eDiscovery tools can proactively identify potentially problematic language and behavior. As well as identify they key facts of an alleged incident or pattern of behavior in a whistleblower situation.
- Fraud Investigations: Fraud investigations may be proactive or in response to regulatory scrutiny. Law firms or in house legal departments can use eDiscovery software to understand the facts of a potential instance or pattern of fraud. eDiscovery AI models can accelerate the process.
- Internal investigations: In internal investigations, speed and confidentiality are key. eDiscovery software helps in-house teams quickly connect the dots on any alleged bad actors. AI-powered eDiscovery software can quickly identify problematic communication, key communicators, and the subjects they are discussing.
- Compliance: As a part of continual monitoring or as a proactive step to avoid regulatory scrutiny, eDiscovery software can identify people of interest or problematic behavior. An example might include looking for harassing language or patterns in data indicative of cartel or bribery issues.
- Human Resources: These tools can be used to identify communication patterns. Uncovering language patterns that indicate pressure, harassment or involve topics that trigger other HR policies.

Show Me The ESI?
eDiscovery is all about uncovering relevant information within ESI. But what sort of electronic data might be potentially relevant ESI and where can you find it? In the beginning, ESI primarily meant electronic documents (word, excel, etc.) and email.
Today, the data sources are much more varied and complex. There are new data types rife with visual content like GIFs, Emojis and video today. Their structure may not much resemble any traditional document. Understanding where you are looking for data and the unique challenges is poses is increasingly important.
The main flavors of ESI in the eDiscovery process today include:

Paper Documents
When Discovery was first popularized with the 1938 launch of the FRCP, paper was the only data source that was covered. The 2006 Amendments and mass digitization of society increased the prevalence of ESI.
This reduced the volume of banker’s boxes of paper in the discovery process but has not eliminated it. Organizations may have decades of potentially relevant information in paper format to this day.

As of 2022, over 330 Billion emails are sent per day. Email has become a primary means of business and personal communication. Despite the growth of other forms of electronic communication, Email remains one of the most important ESI sources. Legal teams anticipating eDiscovery should always include Email in any litigation hold issued.
Electronic Documents
Electronic documents may include spreadsheets, presentations, or written documents. Electronic documents may physically reside on a custodian’s hardware. Sometimes it resides on organizations cloud or in a shared document repository like GSuite, DropBox, SharePoint or O365. Understanding where your digital evidence lives, and the preservation policy helps avoid future discovery issues.

Mobile Device Data and SMS Text Messages
Mobile device data may reside on the physical device, the cloud, in iCloud, or in the environment of the application itself. Effectively identifying and safeguarding the data from deletion is critical. Effective mobile data preservations help avoid subsequent sanctions for spoliation. Be sure to preserve early.
Texting is the dominant communication style of mobile device users, with over 23 billion messages sent daily. The data exported from collection tools may be challenging to understand and quickly review. Be sure to work with a technology that can render the text messages in an easy-to-understand manner.
Legacy Social Media
There are 4.74 billion social media users around the world today, over 59 percent of the total global population! Facebook, Instagram, Twitter, and LinkedIn, constitute the lion’s share of these users and are often a source of potentially relevant ESI.
Social media can contain a wealth of information but also poses unique headaches in terms of identification, defensible collection, and admissibility. As you wade into this social dilemma, it is important to have an expert help you avoid the main landmines.

New Social Media
There has been a recent surge in new Social Media platforms. TikTok, a short format video sharing social media platform has exploded. The app gained 2 Billion monthly active users as of 2022 and generated nearly $5 Billion in revenue. Other emerging Social Media platforms include:
-
-
- Realtime video sharing platform BeReal with 75M monthly active users
- Chatroom based platform Discord with 140M monthly active users
- User generated content sharing social platform Reddit with nearly 500M monthly active users
- Self-Destructing video sharing app SnapChat with 332M Monthly active users
-
These platforms differ from traditional social media in that they are more video content heavy in some cases. Having a clear strategy at the outset to preserve these data sources to prevent spoliation is key.
Collaboration Tools
Since the pandemic, collaboration tools like Slack, Teams, GSuite and more have seen a massive surge in users. These tools are a combination of real-time social platform with multiple topics and group-based channels. As well as the ability to share memes, video, documents and more.
This Slack attack poses opportunities and eDiscovery challenges. The continual and visual nature of Slack and other collaboration tools creates unique eDiscovery challenges.
The data format many export in .JSON can be challenging so ensure your service provider or software is up to the challenge. Collaboration tools require the right type of eDiscovery software, like Reveal 11, to support and effectively visualize.
Short Format Messaging
Over 3 Billion people worldwide use messaging applications like WhatsApp, WeChat, Facebook Messenger. These applications support short format continual communication. People are often more casual when communicating on these application and this can lead to a wealth of potentially relevant ESI. Be sure to see a sample of the messaging data in the review platform to ensure that can be effectively reviewed.

Ephemeral Messaging
Once squarely the domain of James Bond movies, the concept of self-destructing messages has gone from spy trope to mainstream in record time. There are messaging applications that have self-destructing or encrypting capabilities. This further complicates collection and eDiscovery.
Apps like Signal, Telegram, and Wickr can auto encrypt or delete the communications based upon preset rules. These applications, if not properly investigated and/or preserved can create data retention issues. These issues can lead to sanctions for spoliation up to and including adverse inferences as was the case in Uber v Waymo.
Video Conferencing
A final ESI source that has seen massive growth because of the pandemic and WFH revolution is video conferencing. Established tools like Skype and teams as well as new additional like Google hangouts and Zoom have become business critical tools.
Organizations are creating a whole host of discoverable electronic data within them. From the videos themselves to transcripts, chat logs and even shared documents the volume of potentially relevant data can be huge.

Continue reading part 2 next week to learn about specific eDiscovery tools and how they can help non-litigators. As well as eDiscovery pitfalls and what the future of eDiscovery beyond litigation holds.

