Data Privacy, GDPR and HIPAA Violations Fines, and Your Path Forward
Privacy and its kin, data protection and security, are gaining considerable attention these days. With the growth in privacy and data security laws comes a growing risk of penalties and other sanctions. We hear about the risks and we know about some potential penalties, but what numbers might we actually expect to see?
The short answer is that failure to find and address privacy and related issues early on can lead to substantial penalties. Much data privacy legislation is still under development. Of the laws that have been passed in the US, many either are too new or the resulting fines too underreported to help in this context. Two sets of rules and regulations, the newer GDPR and the more-established HIPAA, have enough of a track record to offer insights.
The data about GDPR and HIPAA penalties suggests two points, both discussed in greater detail below. First, in many ways with GDPR, HIPAA, and related directives we still are in early days. As the rules proliferate and become more prominent and publicized, penalties are sure to grow. Second, the GDPR and HIPAA data already available show that criminal penalties can be quite substantial.
What, then, should we do with that information? First, we need to stay on top of existing and emerging data privacy requirements. Second, we should be examining our policies, our procedures, and our practices so that we can align them with the current and coming requirements. Third, we should put in place systems that let us evaluate data already at out disposal, enabling us to identify and from there address problem areas.
Current Rules
The US currently relies on a hodgepodge of hundreds of privacy and data security laws. Existing Federal laws include the Privacy Act of 1974; the Health Insurance Portability and Accountability Act (HIPAA), passed in 1996; the Children’s Online Privacy Protection Act (COPPA), from 1998; and the Gramm-Leach-Bliley Act (GLBA) of 1999.
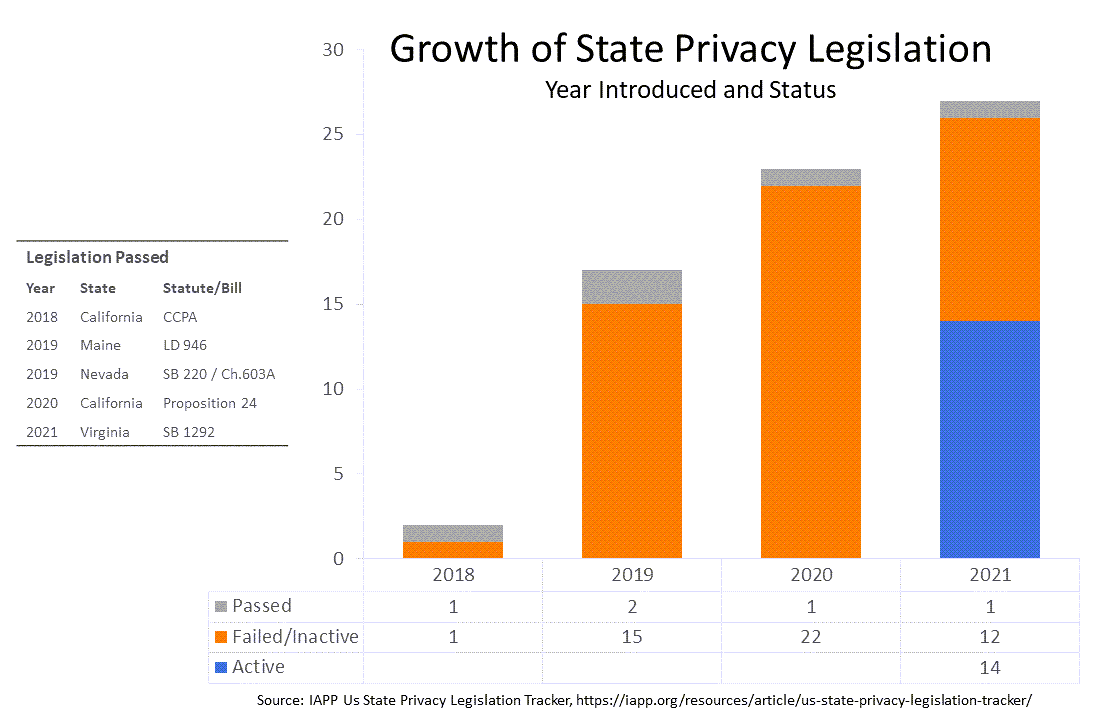
In recent years at least four states have passed privacy legislation, according to IAPPs' US State Privacy Legislation Tracker. In 2018, California, which has more that 25 privacy and data security laws, passed the California Consumer Privacy Act (CCPA); CCPA regulations went into effect earlier this year. In 2019, Maine and Nevada passed state privacy laws, Maine LD 946 and Nevada SB 220. In 2020, California passed a second law, the California Consumer Privacy Act, with an effective data of January 1, 2023. This year, Virginia enacted its own Consumer Data Protection Act; that law also is set to go into effect on January 1, 2023.
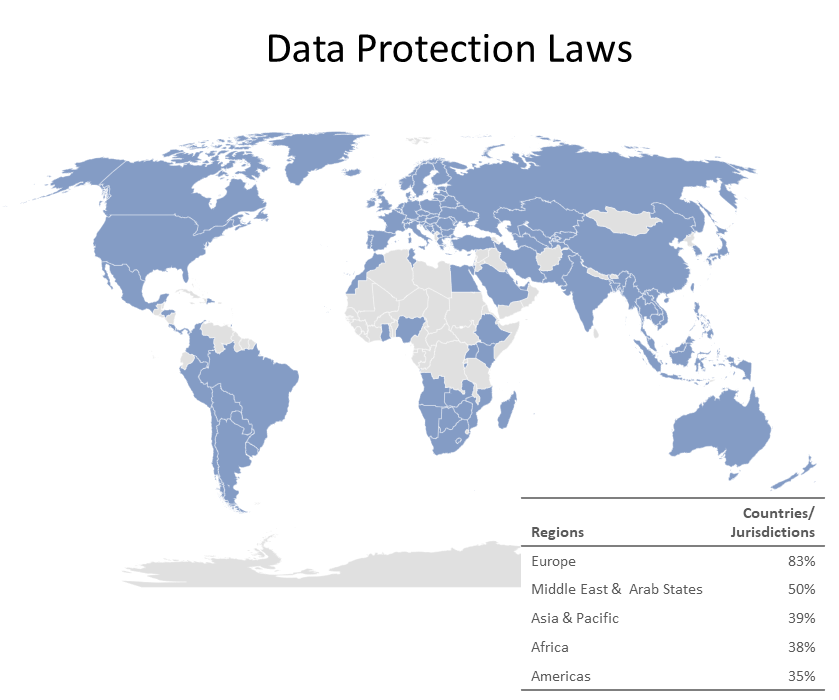
Internationally almost the countries in the world have data protection laws almost the countries in the world - over 120 jurisdictions according to DLA Piper's 2021 Data Protection Laws of the World Handbook, Intrasoft Consulting, and others. Jurisdictions with data protection laws include more than 80% of Europe, half of the Middle East and Arab States, just shy of 40% of Africa and of Asia and Pacific, and about 1/3 of the Americas. The most notable of these laws is the General Data Protection Regulation (GDPR) of 2016, which became applicable starting in 2018.
GPDR Penalties
Penalties for failed HIPAA compliance with privacy rules and regulations can be substantial. The GDPR is the most prominent example. Explicitly designed to make non-compliance costly, the Regulation provides for two tiers of fines. Less severe infringements can result in fines of up to 10M Euros or 2% of a firm's worldwide annual revenue from the preceding year, whichever amount is higher. Fines for more serious infringements can be twice as high, up to 20M Euros or 4%.
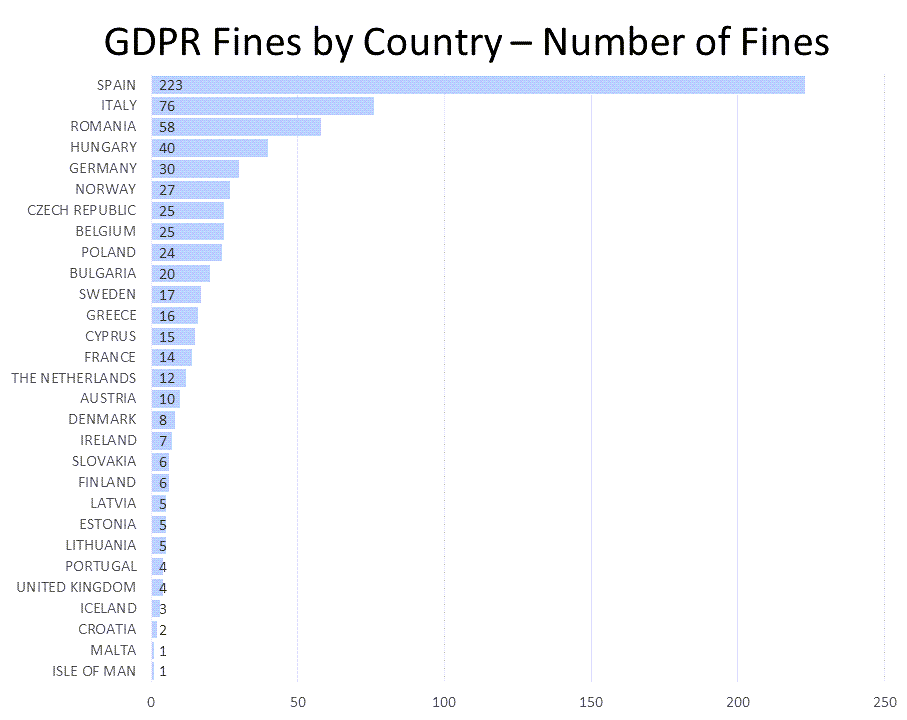
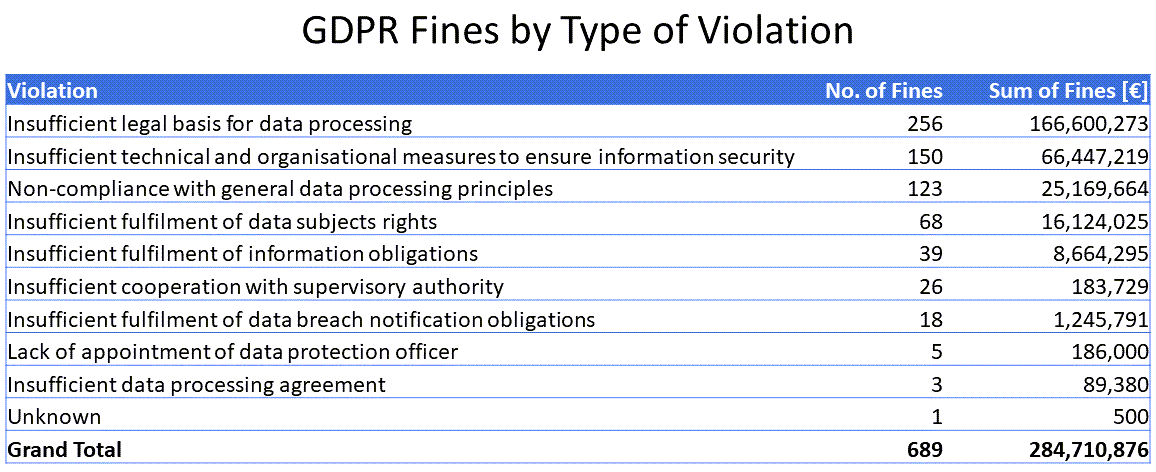
Fines to date exceed 284M Euros, according to the CMS.Law GDPR Enforcement Tracker. The median fines was 10,000 Euros; the average, just over 426,000 Euros. The three largest fines were for 50,000,000, 35,258,708, and 27,800,000, the violation in each of them being insufficient legal basis for data processing.
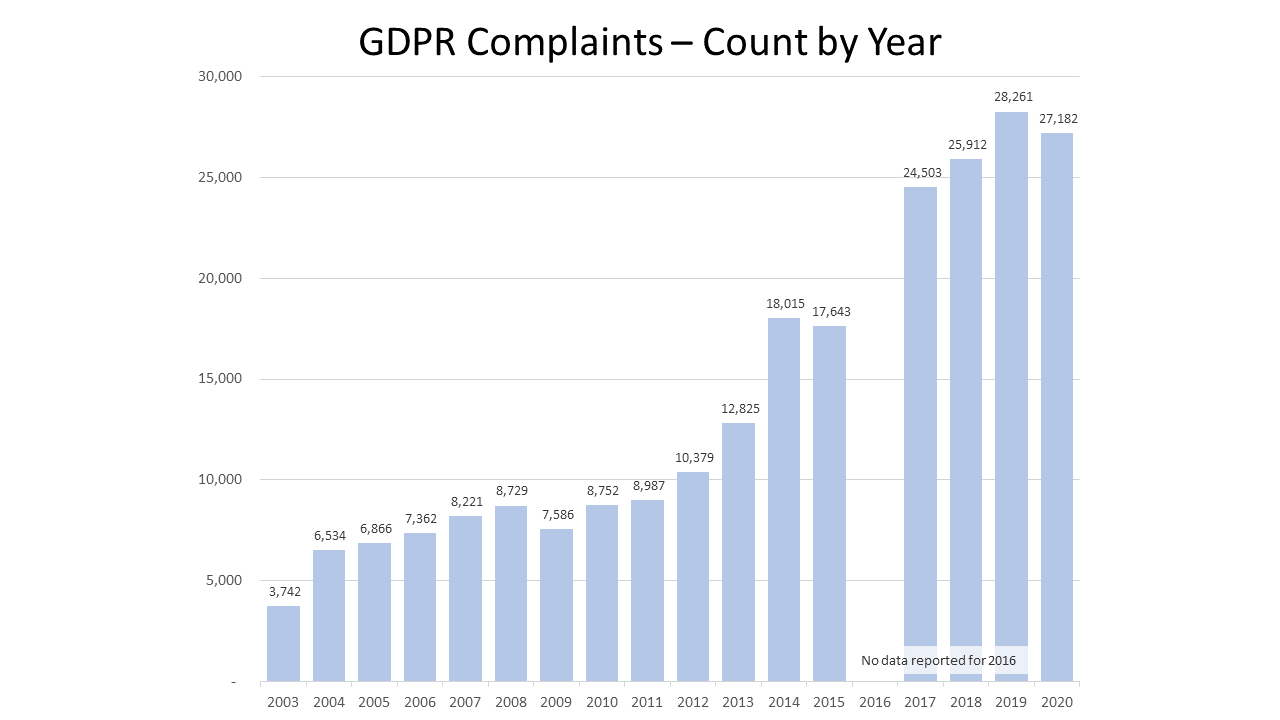
From July 2018 through May 2021, there have been nearly 700 fines imposed in nearly 30 countries, none of them the United States.
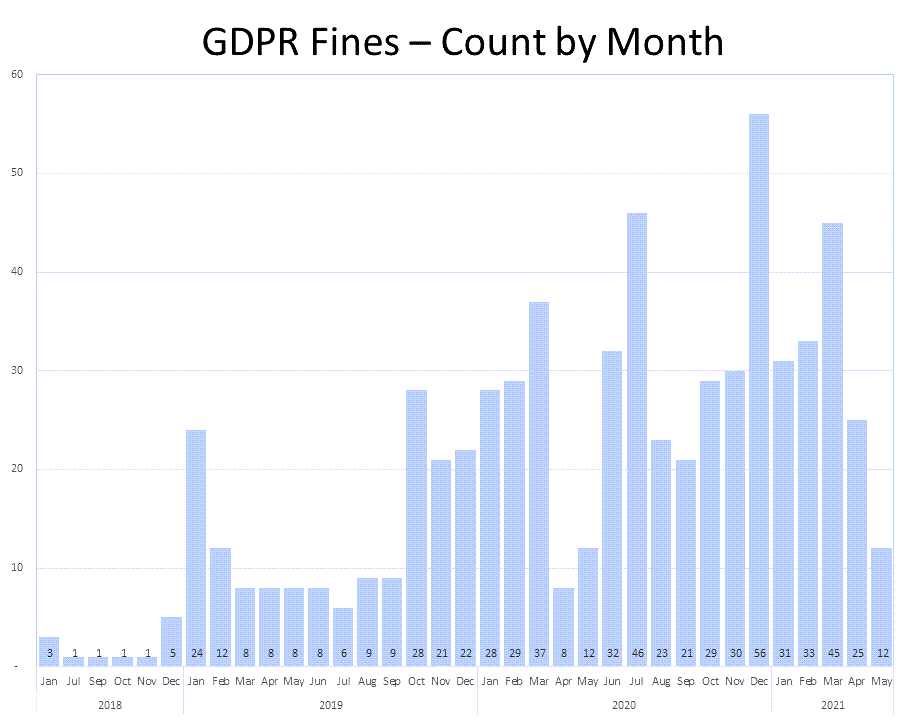
For the past three years, the number of fines imposed has continued to increase.
The most common type of GDPR violation leading to a fine has been "insufficient legal basis for data processing", followed by "insufficient technical and organisational measures to ensure information security" and "Non-compliance with general data processing principles".
HIPAA Penalties
The Health Insurance Portability and Accountability Act (HIPAA), passed in 1996, has been around much longer than GDPR. A domestic privacy law with decades of enforcement in the United States, it's track record provides US-specific guidance not yet available with respect to GDPR.
Upon enactment, HIPAA required the U.S. Department of Health and Human Services (HHS) to adopt national standards to protect sensitive patient health information from disclosure without patient consent or knowledge. These Federal protections included the HIPAA Privacy Rule, to protect individuals' medical records and other personal health data; the HIPAA Security Rule, to protect individuals' electronic patient information; and the HIPAA Enforcement Rule.
The HIPAA Rules
There are three key HIPAA rules:
The HIPAA Privacy Rule, published in December 2000, modified in August 2002, and effective as of April 14, 2003, sets national standards to protect individuals' medical records and other personal health information.
The HIPAA Security Rule, published in February 2003 and effective on April 20, 2005 (and for small health plans, a year later), sets national standards to protect individuals' electronic personal health information created, received, used, or maintained by a covered entity.
The HIPAA Enforcement Rule, entered into the Federal Register on January 25, 2013, contains provisions relating to compliance and investigations, imposition of civil monetary penalties for violations of the HIPAA Administration Simplification Rules, and procedures for hearing. The Enforcement Rule is intended to strengthen the privacy and security protections established under HIPAA for individual's health information maintained in electronic health records and other formats.
Who Needs to Follow the HIPAA Rules
The HIPAA regulations apply to three types of covered entities - health plans, health care providers, and health care clearinghouses - as well as their business associates.
Health plans include health insurance companies, HMOs, company health plans, and certain government programs that pay for health care such as Medicare and Medicaid.
Health care providers are health care providers (doctors, clinics, hospitals, psychologists, chiropractors, nursing homes, pharmacies, and dentists) that conduct certain business electronically (such as electronically billing heath insurance).
Health care clearinghouses are entities that process health nonstandard health information they receive from another entity into a standard format, or process health information from a standard format into a nonstandard one.
Business associates of covered entities also are directly liable for compliance with certain of the Privacy and Security Rules' requirements. Most health plans and health care providers use the services other persons or businesses to help carry out their health care activities and functions; those other persons and businesses are "business associates" under HIPAA. The Privacy Rule allows covered providers and health plans to disclose protected health information to those business associates for limited purposes and if certain conditions are met.
Not all organizations that have individuals' health information are required to follow the Privacy and Security Rules. Exempted organizations include life insurers; employers; workers compensation carriers; most schools and school districts; many state agencies; most law enforcement agencies; and many municipal office.
What Information is Protected Under HIPAA and How
Per HHS, the following heath information is protected under HIPAA:
- Information your doctors, nurses, and other health care providers put in your medical records;
- Conversations about your care or treatment that your doctor has with nurses and others;
- Information about you in your health insurer's computer system;
- Billing information about you that your clinic has; and
- The big catch-all, most other health information about you held by those required to follow HIPAA laws.
To protect health information, covered entities are required to:
- Put safeguards in place to protect health information;
- Ensure that they do not use or disclose health information improperly;
- Reasonably limit use or disclosure of health information to the minimum necessary to accomplish the intended purpose;
- Put procedures in place to limit who can access and view health information;
- Implement training programs for employees about how to protect heath information.
Similarly, business associates are required to put safeguards in place to protect health information and ensure they do not use or disclose health information improperly.
Permitted Uses and Disclosures
Covered entities are permitted to use and disclose protected health information without an individual's authorization under certain circumstance and with reasonable cause. These include, as summarized by the Centers for Disease Control and Prevention and described in greater detail by HHS:
- To the individual: Disclosure to the individual who is the subject of the information;
- For treatment, payment, and healthcare operations: Use or disclosure by a covered entity for its own treatment, payment, and healthcare operations activities and in related situations;
- With opportunity to agree or object: Permission obtained informally, by circumstances that give the individual the opportunity to agree, acquiesce, or object, and in emergencies where the individual is incapacitated;
- Incidental: Use or disclosure that occurs as a result of or incidental to an otherwise permitted use of disclosure;
- For public interest and benefit activities: For any of 12 national priority purposes: (1) required by law, (2) public health activities, (3) victims of abuse, neglect, or domestic violence, (4) health oversight activities, (5) judicial and administrative proceedings, (6) law enforcement purposes, (7) decedents, (8) cadaveric organ, eye, or tissue donation, (9) research, (10) serious threat the health or safety, (11) essential government functions, and (12) workers' compensation.
Enforcement Under HIPAA
Since 2003, HHS' Office for Civil Rights (OCR) has borne responsibility for enforcing the Privacy and Security Rules for most covered entities in order to prevent patient data breaches. ORC carries out these responsibilities several ways, including:
- Investigating complaints filed with it;
- Conducting compliance reviews;
- Performing education and outreach; and
- Working with the U.S. Department of Justice (DOJ) to refer possible criminal violations of HIPAA.
Once OCR decides to take action on a complaint of HIPAA noncompliance, it goes through the following process:
For OCR to take action on a complaint, the complaint must meet the following conditions:
- About activity after 2003/2005: The alleged action must have taken place after the effective dates of the Privacy Rule (April 14, 2003) or the Security Rule (April 20, 2005);
- Against covered entity: The complaint must be filed against a covered entity;
- Violated Privacy or Security Rule: The complaint must allege an activity that, if proven true, would violate the Privacy or the Security Rule; and
- Within 180 days: The complaint must be filed within 180 days of when the person submitted the complaint knew or should have known about the alleged violation.
Once OCR accepts a complaint for investigation, it notifies the person who filed the complaint and the covered entity named in the complaint and seeks information from them. Should the complaint describe an action that potentially violated the criminal provision of HIPAA, OCR might refer the complaint to the Department of Justice.
The next step is for OCR to review information it gathers. It might determine that the covered entity did not violate the Privacy or Security Rules, at which point it would close out the complaint.
If the investigation indicates that the covered entity was not in compliance, OCR will try to resolve the case by obtaining some combination of voluntary compliance, corrective action, or resolution agreement.
Should OCR not be able to obtain a satisfactory resolution such as the covered entity demonstrating a willful neglect of HIPAA rules or committing data breaches for personal gain, it may decide to impose civil money penalties (CMPs) on the covered entity.
Settlements and Fines Under HIPAA
Office for Civil Rights (OCR) Settlements and Fines
From April 2003 through March 31, 2021, OCR received 259,972 HIPAA complaints.
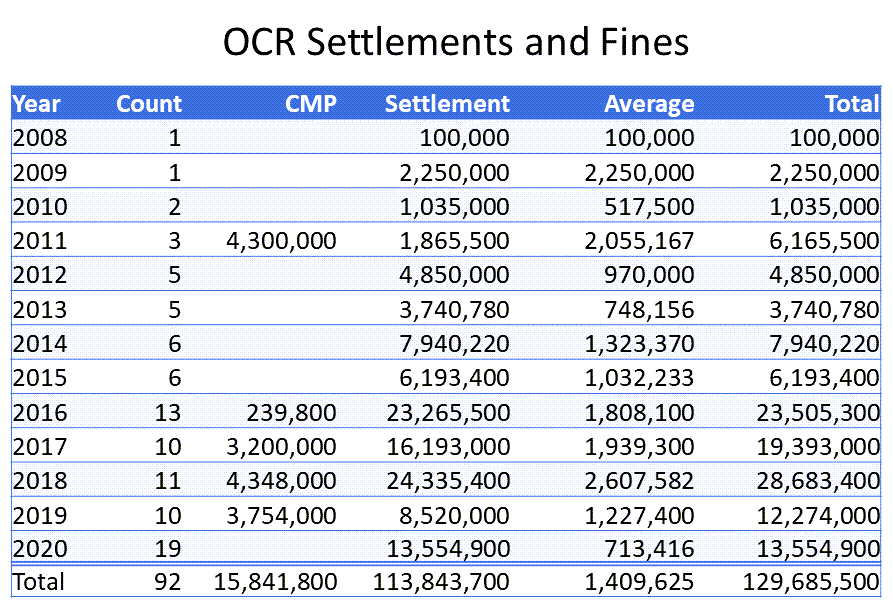
OCR resolved 99% (256,086) of the complaints. In 99 cases, resolution meant settling the matter or imposing a CMP. The total amount of financial penalties, including both fines and settlements was $135,298,482.
HIPAA Journal maintains a list of OCR settlements and CMPs from 2008 through 2020 and a list of Attorney General HIPAA fines and settlements from 2010 through 2020.
HIPAA Journal lists 92 OCR settlements and fines. The number of HIPAA violation fines and settlements stayed in the single digits annually from 2008 until 2015 and rose to double digits annually after that. Together, OCR fines and settlements tracked by HIPAA Journal have totaled $129,685,500. Of that, settlements accounted for $113,843,700 and CMPs for $15,841,800. The median settlement was $507,500; the average, $1,323,764. For CMPs the median was $2677,000 and the average, $2,640,300.
Numerous reasons were cited as the bases for issuance of the fines and settlements by OCR. While in most situations only one or two reasons were cited, in some matters multiple HIPAA breaches were offered. The most frequently-mentioned reasons fit into five overlapping groups:
Access issues (22 matters): HIPAA Right of Access failure; denial of access; insufficient access; failure to terminate access; and insufficient access controls.
Risk analysis/risk assessment issues (19): Failure to conduct risk analysis; risk analysis failure; risk assessment failure.
Disclosure issues (17): Impermissible disclosure of PHI and ePH including 3.5 million records, 307,839 individuals' PHI, 6,617 patients' ePHI, and PHI of 498 individuals; unauthorized disclosure; disclosure without patient consent; social media disclosure; and PHI disclosure to reporter.
Safeguarding issues (14): Failure to safeguard PHI and ePHI; lack of HIPAA safeguards; and failure to implement appropriate administrative safeguards; lack of admin, technical, and physical safeguards.
Business associate issues (12): Lack of business associate agreement; business associate agreement failure.
Attorneys General HIPAA Fines and Settlements
HIPAA Journal lists 33 Attorneys General fines and settlements for the years 2010 through 2020 (albeit with no information for 2016). This matters tended to be larger both in terms of how many people were affected per event and how much money was involved.
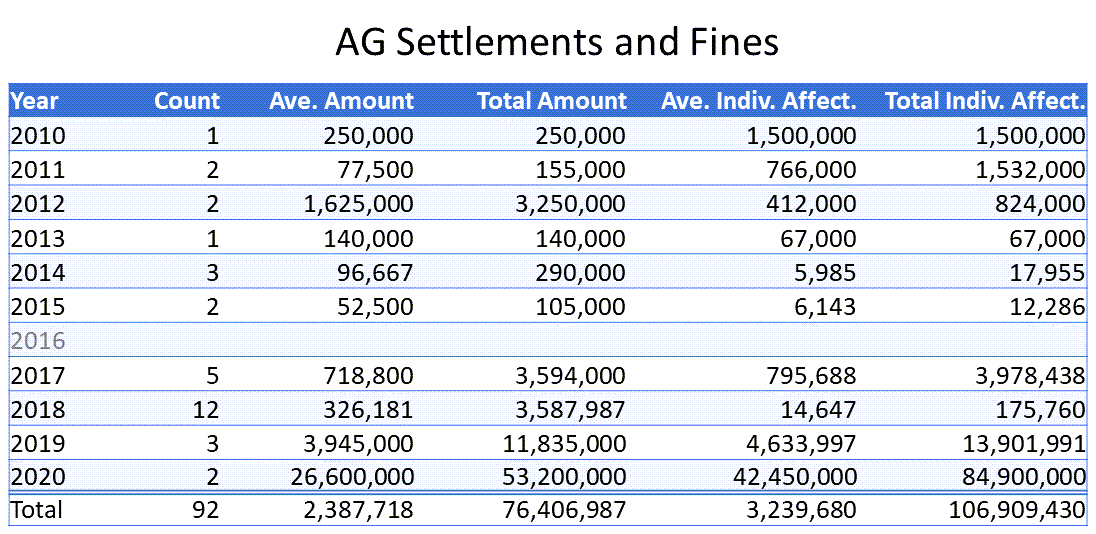
Reasons for AG fines and settlements align with those for the OCR ones. They include violation of HIPAA rules such as mailings of exposed PHI, loss or theft of unencrypted equipment, delay or failure to report issues, inadequate security practices, and improper disposal of data.
If your healthcare organization is interested in leveraging AI models, pattern recognition and machine learning to find your potential privacy challenges before they become major penalties, contact Reveal to learn more. We’ll be happy to show you how our authentic artificial intelligence takes review to the next level, with our AI-powered, end-to-end document review platform.

